I got a little time to start looking at this.
Anyway, I replaced the cert and key:
This is the key and cert I made the other day:
/*
const char *cert_pem = "-----BEGIN CERTIFICATE-----\
MIIF3TCCA8WgAwIBAgIUPNMkwDcT1pkDihebaQfebG/5CxMwDQYJKoZIhvcNAQEL\
BQAwfjELMAkGA1UEBhMCVVMxDTALBgNVBAgMBElPV0ExEjAQBgNVBAcMCU1VU0NB\
VElORTEXMBUGA1UECgwOV0hFUkUgTEFCUyBMTEMxEzARBgNVBAsMCkJVUyBQSVJB\
VEUxHjAcBgNVBAMMFWh0dHBzOi8vYnVzcGlyYXRlLmNvbTAeFw0yNTAxMjkxNDI5\
NTZaFw0yNjAxMjkxNDI5NTZaMH4xCzAJBgNVBAYTAlVTMQ0wCwYDVQQIDARJT1dB\
MRIwEAYDVQQHDAlNVVNDQVRJTkUxFzAVBgNVBAoMDldIRVJFIExBQlMgTExDMRMw\
EQYDVQQLDApCVVMgUElSQVRFMR4wHAYDVQQDDBVodHRwczovL2J1c3BpcmF0ZS5j\
b20wggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCmpTSnVyvhIyEJEhUP\
mjxdOewyT3cmZE1X7LcnEqGYoFa2KUtj9b6z+h2zfgsqbIt14Zv/eDK3/SW9mmp8\
20kRx5cE2bUzNXVz343nBia16eO/qn1DEmfGFKTkt48yhWvzFM4CScWOlLDv7b6h\
XDFa3iX1i/0xvi4SN1o6t3PoSEE4AjdDKlN8g50lsHEdMQmV+J9OvL68P+Iy/A7f\
nUeuyF3SegZ2T/9pa5vgnliPCVAzMTl4OWWRhr5XsfydGhaUcU2W8LpfSh1cERjl\
72EiSMkFfQa2li1rS2iHcCf9AT05CJnU5WNMd9/q4gyZ7K7yoaqsknVYYVIglbIw\
KHK4n/TUZQnmNSo+491hkxLkhrLC7LjLVtT5LC7Sp8ZbYWs51Tp4x4/qBnEzCXr9\
OrIuIOacvDjGybl5G5Hvy1PauyGYpqrEb/dIsBKm8VlUJCEsN8rbxcGfGTuBusVv\
6v65EdzsxCWuNNslJvVl5f6amzWkTLNW3McFv7ID90y/iQPfybod5CKYUo3zfLA5\
kHJVR9P5vW9gKuIWUZE75Q9cXkSq+t9ExHc8jOhWZpSvFNd/qhkRi5B4ZxITUA3b\
5aQRHZuHFEFrNx8oRBtvEXIACN5INFhURuybKieC0zKFa0K+vR6zAHTzv/Tq4QmU\
qDGbeOychtn3TWUWABwhArKrhwIDAQABo1MwUTAdBgNVHQ4EFgQUSjnuX4w0PMfn\
hHu6UvC5MqdfplAwHwYDVR0jBBgwFoAUSjnuX4w0PMfnhHu6UvC5MqdfplAwDwYD\
VR0TAQH/BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAgEALZH+P93QP7zjczdifdt4\
/hOBrFHjtsktMq5pDBNxrLPdTEJ0EK6IWN+Tj51P31Kn1yJn6xqYFrykMIT0JXBG\
YF8/iGvq+vDnc4FWuxrOVtpyeUGxxW0gblvlgrqDPA+y08lCvnZvzjsZAzYZiEry\
o29EKqhp/VvR2DWJUSkta4bDqn+EAH3JbKVa/avQp8eNVizLfTEVb8nRLNtwV+lE\
i+KyYHwQhVyAFjdSwaT18kP0fFw9kBCDNOmJuPyH8kB3trQMcy2TpDd+3379m+mv\
YfHFpm9NXdQXnJcGmA7nV2REG6CDgF9g5mPDFEGYh6z25zcwEzVUL9BfrZ73fhf2\
fjdhOH7N2zjOdPX8IwuG/SJbUC4UNH5fTt80hQsMo33cL7ukbn//SraCQuP479WI\
QoiUHOXZO8hDLnCs31iE6BTlrDaLyrd6PgTlXmlfhzGeHtQ9/alv+j2WEtWm661Q\
K1w26UicqvVfLbtqCy0PiDgMGE2Wz3bct1v3qy698+sNSrTP/MNmwvTxvIrhgNh3\
GOPbbu5h9DOtZdim5+KGnEk9JQRI90AOuCcW2eiu8Z0JZhRV3v6MMmIFvE4odB0x\
ogeb1DKjKhB3iCbU23yiyN0wxRmKEPTxlxoEsisx8/7PXtqY48K41m//1yavuLeY\
wrK6PPSRSHUXxZmvLVLMf0M=\
-----END CERTIFICATE-----";
*/
const char *cert_pem = "-----BEGIN CERTIFICATE-----\n"
"MIIDtTCCAp2gAwIBAgITaKShdq9xXbBofxeT8mpjU4xFQjANBgkqhkiG9w0BAQsF\n"
"ADBgMQswCQYDVQQGEwJVUzELMAkGA1UECAwCV0kxIzAhBgNVBAoMGk1hdHR5ZHlu\n"
"ZSBIZWF2eSBJbmR1c3RyaWVzMR8wHQYJKoZIhvcNAQkBFhB0ZXN0QGV4YW1wbGUu\n"
"Y29tMB4XDTI1MDEyOTE2MTQxMVoXDTM1MDEyNzE2MTQxMVowYDELMAkGA1UEBhMC\n"
"VVMxCzAJBgNVBAgMAldJMSMwIQYDVQQKDBpNYXR0eWR5bmUgSGVhdnkgSW5kdXN0\n"
"cmllczEfMB0GCSqGSIb3DQEJARYQdGVzdEBleGFtcGxlLmNvbTCCASIwDQYJKoZI\n"
"hvcNAQEBBQADggEPADCCAQoCggEBAM46AUpYay/BiKKXDnwdS9wI6yBYz6NClxWV\n"
"vXhbs/I2Y/AH+A8ZmHnMYb0B9rSXRXyI5Ar3dTvultmJJ4qr6aibxvl99p7jmp0U\n"
"MieX6EasClC+vmpzUTHTWMoGWy2eviyqbK+tnO5sD754DiAp8PgHdVq3E0rdoF6k\n"
"bidmZLhdQD3CEmlSnPFllB2nELT//B18PE3jIf7iBU9Klbz6xS9iU5bM/g0R21yx\n"
"69udOY1crREaWgBBH+1x0dfYyGNa3yVfgIIGfLk9mT3MTD1IlaI0JXAET7r5pcnt\n"
"rW2l54ECaZ08SA9O0heKWWz3zrnGtXMemzNxx8AkKoinSqI0tbUCAwEAAaNoMGYw\n"
"HwYIKwYBBAGh9CMEEwwRQlAgc2VyaWFsIDEyMzQ1NjcwJAYIKwYBBAGh9CQEGAwW\n"
"clBJIHNlcmlhbCBhMWIyYzNkNDk5OTAdBgNVHQ4EFgQU/nqKhpUnDq82nl4lGYoO\n"
"fCRlr3EwDQYJKoZIhvcNAQELBQADggEBAE6FUOZ2Wg/L5AG3UDqnpoX3FM6aLu7i\n"
"IGnr8G+Ru9rxEQaIISPGdH2m3jaebM8AoZGLRhJooAev03AoiWuIJXSQB4nEQvSr\n"
"DqOxf2KvkTcwaghjisr+duRQ3kkAM5xqxV1WjiL0jdE42t6FwesU0y45/UnMe8iQ\n"
"ON+sd9b4xChgRS5g7dPK2XdMxJYeUNAEICKBSQeUWY7BRa3A50dHR23n5Xio5Rcy\n"
"hZAiCQ7pLUUjjehcvmUVBG9PR7RPMNSkB6N0fd8GUwSl2fy+VG/BaScO68rUf0qj\n"
"U0r95j0j1GsySuTRk16UMC9WBPqfPvUROOHrMXoT3cpTAVvl041WOsE=\n"
"-----END CERTIFICATE-----";
/*
const char *public_key_pem = "-----BEGIN PUBLIC KEY-----\
MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEApqU0p1cr4SMhCRIVD5o8\
XTnsMk93JmRNV+y3JxKhmKBWtilLY/W+s/ods34LKmyLdeGb/3gyt/0lvZpqfNtJ\
EceXBNm1MzV1c9+N5wYmtenjv6p9QxJnxhSk5LePMoVr8xTOAknFjpSw7+2+oVwx\
Wt4l9Yv9Mb4uEjdaOrdz6EhBOAI3QypTfIOdJbBxHTEJlfifTry+vD/iMvwO351H\
rshd0noGdk//aWub4J5YjwlQMzE5eDllkYa+V7H8nRoWlHFNlvC6X0odXBEY5e9h\
IkjJBX0GtpYta0toh3An/QE9OQiZ1OVjTHff6uIMmeyu8qGqrJJ1WGFSIJWyMChy\
uJ/01GUJ5jUqPuPdYZMS5Iaywuy4y1bU+Swu0qfGW2FrOdU6eMeP6gZxMwl6/Tqy\
LiDmnLw4xsm5eRuR78tT2rshmKaqxG/3SLASpvFZVCQhLDfK28XBnxk7gbrFb+r+\
uRHc7MQlrjTbJSb1ZeX+mps1pEyzVtzHBb+yA/dMv4kD38m6HeQimFKN83ywOZBy\
VUfT+b1vYCriFlGRO+UPXF5EqvrfRMR3PIzoVmaUrxTXf6oZEYuQeGcSE1AN2+Wk\
ER2bhxRBazcfKEQbbxFyAAjeSDRYVEbsmyongtMyhWtCvr0eswB087/06uEJlKgx\
m3jsnIbZ901lFgAcIQKyq4cCAwEAAQ==\
-----END PUBLIC KEY-----";
*/
const char* public_key_pem = "-----BEGIN PUBLIC KEY-----\n"
"MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAzjoBSlhrL8GIopcOfB1L\n"
"3AjrIFjPo0KXFZW9eFuz8jZj8Af4DxmYecxhvQH2tJdFfIjkCvd1O+6W2Ykniqvp\n"
"qJvG+X32nuOanRQyJ5foRqwKUL6+anNRMdNYygZbLZ6+LKpsr62c7mwPvngOICnw\n"
"+Ad1WrcTSt2gXqRuJ2ZkuF1APcISaVKc8WWUHacQtP/8HXw8TeMh/uIFT0qVvPrF\n"
"L2JTlsz+DRHbXLHr2505jVytERpaAEEf7XHR19jIY1rfJV+AggZ8uT2ZPcxMPUiV\n"
"ojQlcARPuvmlye2tbaXngQJpnTxID07SF4pZbPfOuca1cx6bM3HHwCQqiKdKojS1\n"
"tQIDAQAB\n"
"-----END PUBLIC KEY-----";
And the results:
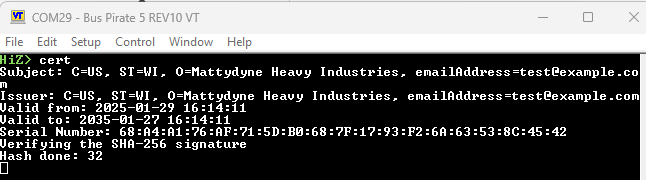
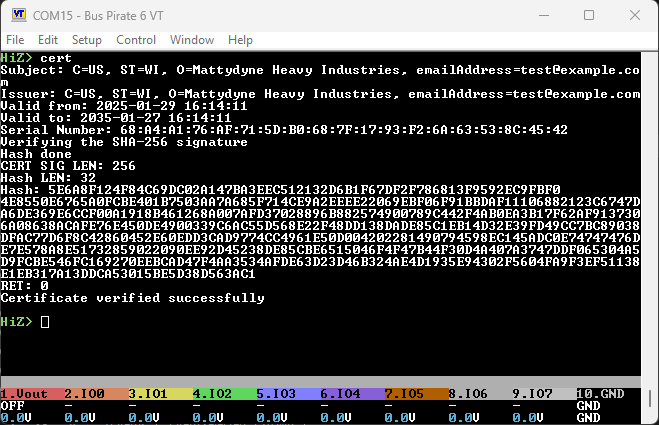
HiZ> cert
Verifying the SHA-256 signatureHash done
Subject: C=US, ST=WI, O=Mattydyne Heavy Industries, emailAddress=test@example.com
Issuer: C=US, ST=WI, O=Mattydyne Heavy Industries, emailAddress=test@example.com
Valid from: 2025-01-29 16:14:11
Valid to: 2035-01-27 16:14:11
Serial Number: 68:A4:A1:76:AF:71:5D:B0:68:7F:17:93:F2:6A:63:53:8C:45:42
Certificate verified successfully
HiZ>
I was seeing both cores hang as you described until I changed the cert & key.
At least it’s some progress!
I’ll play with the python script and make some certs to see what happens, (but I may not look until tomorrow or Sunday, depending on the grandkids’ soccer and the like ![]() )
)
Just thinking about this before I shut down … Maybe mbedTLS doesn’t like the 4096 bit key? Mine is a 2048.