I’d love to see the BP print a snarky comment if it booted up and realized it was a cheap clone. ![]()
“For best results, use Genuine Dangerous Prototypes products!” ![]()
The Ring oscillator and Low Power-osciallator are just used for booting the RP2350. On the Bus Pirate (and on most other circuits as well) the crystal oscillator then fully takes over and the ring osciallator isn’t used for anything afterwards. So for the BP a frequency deviation in these wouldn’t matter as long as the chip is able to boot up. And these values would have to be completely off to prevent that.
It is possible to use the RP2350 without a crystal oscillator. For example just use the low power osc during sleep modes and then still use a UART in this mode or something. Or not use a crystal oscillator at all to save costs or pcb space. Then these calibrations would matter. But not for the BP.
PLEASE do not really suggest this!
The point is to help Ian when issues arise (tracing issues back to common cause), and/or help users discover if a board is affected by a known issue (e.g., Does my BP6 have the E9 fix?). This can be done by having the manufacturing data.
A snarky comment is counter to the open-hardware ethos that, if I understand correctly, Ian is fully supporting. I like the term “Certificate of Provenance” … it says where it came from. It seems Ian allows his hardware to “speak for itself” … and I’ve been happy with its quality.
If you’re really trying to outmanouver the cloners, then the threat model needs to be reworked in a significant fashion. Everything done with hardware dongles (HSMs, FIPS compliant, tamper-evident, etc.) that generate CSRs; Root key setup using M-of-N hamming codes, to allow loss/destruction of (N-M) of those hardware dongles; 100% offline-only computer interacting with any root key HSM hardware; Intermediate level certs acting as targeted CAs, … etc.
That said, I think it’d still be fine to skip multi-party aspects (each of the N root dongles with different party), the faraday cage for the offline root operations, etc. ![]()
No, for my part the “buy genuine” was tongue-in-cheek.
But seriously; it’s not about out manoeuvering counterfeiters, it’s about recognizing and protecting the DP brand. Great quality matched with even better support.
It’s a bit of fun to joke about a snarky or even satirical comment, but not something I meant in earnest. Sorry about that; sometimes tone doesn’t come across as intended.
Thanks for bringing this up and bringing us back in task in this regard. ![]()
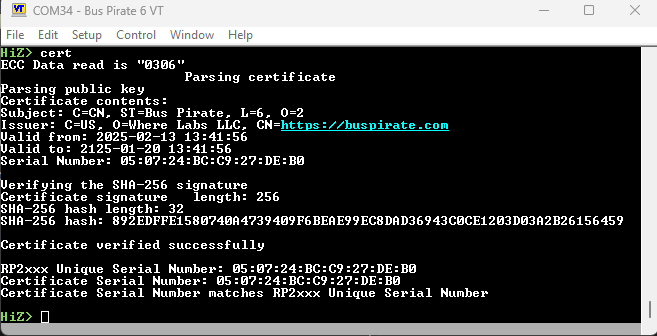
HiZ> cert
Parsing certificate
Parsing public key
Certificate contents:
Subject: C=CN, ST=Bus Pirate, L=6, O=2
Issuer: C=US, O=Where Labs LLC, CN=https://buspirate.com
Valid from: 2025-02-07 13:42:55
Valid to: 2125-01-14 13:42:55
Serial Number: 4E:1A:62:90:F8:7E:B4:B8
Verifying the SHA-256 signature
Certificate signature length: 256
SHA-256 hash length: 32
SHA-256 hash: 0A7ACFF1C713B3999CDDDB9D481806A1038CE5078EA6757DA7C4164CB114FF16
Certificate verified successfully
RP2xxx Unique Serial Number: 4E:1A:62:90:F8:7E:B4:B8
Certificate Serial Number: 4E:1A:62:90:F8:7E:B4:B8
Certificate Serial Number matches RP2xxx Unique Serial Number
HiZ>
This is a much reduced cert file, eliminating extensions and some fields. It is also about 25% smaller.
- Subject: C=CN (manufacture country)
- Subject ST=Bus Pirate (device name)
- Subject L=6 (hardware version)
- Subject O=2 (hardware revision)
- Issuer: C=US (issuer country)
- Issuer O=Where Labs LLC (issuer name)
- Issuer CN=https://buspirate.com (more info website)
- Valid from = 2025-02-07 13:42:55 (manufacture date)
- Serial Number: 4E:1A:62:90:F8:7E:B4:B8 (the RPi chip unique ID)
If you would like your very own cert, post your serial number ![]()
cert.zip (2.3 KB)
Latest python program. Has some error handling for incorrect private key password. Command line arguments are --serial <hex format serial 16 characters> and --passphrase
Nice! Looks great.
I’ll have to finally break down and buy a 6 now! ![]()
Or a PICO2 board ![]()
Not enough characters.
Oh, good point!! Yeah, that would be good to play with. I’m away from home; I’ll get next to it next week.
Key generated
Subject: CN=Shenzhen HuaHong Assembly Co.\, Ltd.,O=2,L=6,ST=Bus Pirate,C=CN
Issuer: CN=https://buspirate.com,O=Where Labs LLC,C=US
Valid from: 2025-02-07 16:32:35
Valid to: 2025-02-17 16:32:35
Serial Number: 6661e5bbdaa5df5
Public Key: -----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAychgXZzKDiZVcbqDz9sY
5y8MlWP0lEe0A+Lp2hkaCXJAP3buk7pUSe11Rv1GWepyPy4lg0hgflLOTcAisHV3
/OpV7vppd2lIwiYo6agnGggA7aYk77kYgY45Xlv2B1Sc1uLp93xUGbnmOsg0Zran
q2Rkyv0aP6Sau/34L7/803yIQ96f5H2ibLGzf+YG5SvdU+tQnU0PPW876mZnFReY
I1oyEVQZKDg2SLV7cYhN6niqCIjpO1ayfSoC/GR8lfZN4Uux4okpJcsXnUnAARcB
hpsVUBr4173QQTMl/+iL14BfGaD4Z1A72CDYbIrA7THw7+cjY4ZhdIUmqOGrWhYE
gQIDAQAB
-----END PUBLIC KEY-----
Station certificate created
Encrypted Request: 3ec9802c3a85cc595cc41989282b095c00de122977ac46c6574e1f3d2c21662659e244063f5213711bf43b105b0d4b215ff1e393247247f59d40b6da9490351939bd4f67cd95f3a82ac4f34c6abdd75bc369f526a98ea84315fd1d881c52ab6b4b6d8694d8a9113813abb3b01f06b709ffb860b45ed21ba3faa7d2e9e3f8eb6fe369701db241daf81ef9bfa4e66c8c5f69c9881ed3393707d5388dd9523768c5c1dbc20351ea32dbd8b6b19f2a81eebe11bf518ff069c8b3e41002f71a1b7c1aebfb08c70ac2d086a7ef799240b55abdcdf69cc670a5e4800fca1cf71fa15065207c5cb16aeb66d86cb9fdea3db9d54e2a1b5a963d6565b5fbf253d0708dc509
Key loaded
Decrypted Request: {'serial': 461089391224970741, 'station': 1}
Took a stab at making the programming station side:
- Generate a new “station” private key (different than the Bus Pirate private key). Not sure this is needed. I think so to rotate keys, but maybe the certificate is enough?
- Create a short life certificate for the programming station, signed by private key
- Station encrypts the RPi serial number with the public key and sends a request to the server. Perhaps I should include the cert in this to verify the validity instead of issuing multiple private keys and revoking the public keys?
- Server decrypts with the private key and if valid creates a new Bus Pirate certificate and sends it back to the programming station.
It’s kind of a mess of code at the moment, some concepts are not yet clear to me. I’m inclined to include the cert in the transaction so the server can verify the validity without tracking multiple private keys.
Welcome any thoughts from you pros!
EDIT: I believe huge parts of this include misconceptions. I need to think it over a bit.
I have thoughts, but need to draw diagrams to check and share them. I won’t be able to get to that until Monday ![]()
We need to diagram the trust boundaries and show key/data flows to really understand it all. It gets confusing quickly!
I’ve been doodling as well. It feels like I’m half way. Protecting in transit, but no verification of origin.
It seems like the programming station should be issued a temporary private key, the details stored in the server.
Programmer issues a cert signed by private key including RPI ID, then encrypted with server public key.
Server decrypts and verifies very with stored public key. The BP cert encrypted again with programmer private key.
That seems to protect in transit while verifying both sides of the transaction as well.
Have a good weekend!
station.zip (3.9 KB)
Prototype station->server->station interaction
ian@DESKTOP-7VKKLTO:~/cert$ python3 station.py --serial 4e1a6290f87eb4b8 --passphrase 123456789
#############################################
Server Side Operation
Server private key generated
Server public key saved
#############################################
Station Side Operation
Station private key generated
Saving station public key
Certificate created for: 4e1a6290f87eb4b8
Subject: CN=Shenzhen HuaHong Assembly Co., Ltd.,O=2,L=6,ST=Bus Pirate,C=CN
Issuer: CN=https://buspirate.com,O=Where Labs LLC,C=US
Valid from: 2025-02-08 16:45:45
Valid to: 2025-02-18 16:45:45
Serial Number: 4e1a6290f87eb4b8
Public Key: -----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA57/dKGca6vWCM5nF7+V6
Q5/d6lPah3e72kXg3tJosl6fsohMFx4pyVNVU2N5fdKlnIL19aRJuAF0zjdeVQPq
EPSGchfI9GIUme+u23ETVgmZQKW8YRW74jEvSJApXYPl1krnpUwB+j1K+PO/owmy
RnqDYatPVKKkvvZpde4D6YozTOS5poR6KCsBYK8CbqeBuS8F4egvhXtqoP6IqxCW
222fjoxMXZOfT9MGvcuo2rfOH/M64UBi0Lw0bLaEekBj72uypZpVztuzcVoi+Req
mEdPlnLUCn3WeMNlmHv2TOjOL9G9f9qHh8gYRv+3kgf7hd7WHM7a9sd0ag9ak31w
3QIDAQAB
-----END PUBLIC KEY-----
Loading server public key
Encrypted AES Key: 5a814e6b253f25b58a9a2ca1714a77568639b5966c9b4082f003fccfdb168c0b412ce1f044ca84d192132547df69641db643656a85ea448d1e4a78a54e77f90cc02c7a084e5baf550fa7daec54ed1bb80c32b68db22c5c3d836e12e3c4e3b5bc77253445a246041141968267f00a508d1102315216a8af2ced192c8fe305188255f97ba97ae474b01e5a45a00362eb4558f2af263b39a962e3013457d888e17ee16c5bf533703a351a7dcb362bf02cfa8aff6f125de85fee25ad4c7c1dc907ad4c1a25a6cef0915b24bfcf91ce8887df922a0c769cc1b7dd576f1e7548a9ed500047a73139b6192561582bce1a7495f12128435dcd17c82709839ef0a982e4d8
IV: c201a0abfdea8455597ffedf5b7fe4f1
Encrypted Request: da251e86302c97ace00db3e975569287924898927024ef15c03681f138ad70b7a0360eff52a004235c6a9bf4d4265e69be625559a49cc44238f402e93a7ab16c3919d166d8091a37df0d6aa56a43020b5e27e8b238e3795adb82d7a96aa7a4186004ac1e9a01dc10373db96376c9f37896de075445cfb7a9ff29aff4b8a0a4cc1a5b3c723b6b58cf279ee1257c388d3128935848a8d22c087580c8cc66a9d269f1bc39f2211d1cf905a7b9ad68ff57f48a6c078282f7aab77d53e6449a4db7d26d59a12f9c28b78b831cab0258fdfc1beee24d115b8e6193ad0a9b5074b3f9a75d49e742d45e3ecded634ccf647deab10e996f778ae404404498bdbd8ba50a17cbf90e97f64c839f64476036af2dbf826377d6642956520dd3415405c31874d4daac31d8d4b18046f95ddb51625ef2c678880ee2a778955ae040f0e6e4d85ad1e42bbd4be7cad4fdc0016623e972258b2b903ecd85f6ed35a59fc7fbd94a99ed0416adb5f8ba7656fed5f4a339abca146e4013634f3ba2e73682184b8d0d838b00b5d7b4af19319c96d0173d421d7ba0e867007df6edf8d39d238d6360b1a51d4b4a0ec485f60106f76e6f67188920641128a2053fb647bc9b62c8e82066742eb6259fa4ed18962a56be80ab0cf662a0180971bb35e6224f3ea4115f54262385fa9ccc34dfb8da013c367d2e66ccd527c7d3dd10a25f4777710d3e78cdf571ac1d6c868d8dc69deabec3617ee6b21e1bf0cffb2bdd097c0e1ad562dbca6a2a512aa291286cca6490f878d262cc39dd82bdc798f293fd1461eedbf9cfa07efcff20ccd3495bc7c623a67d067cc6fa8adfc7eeb7e7bbc597159d0d6c84a5e3381690398cd0954ecb67e832092f5d7043f5ec273552aa81e630b352b3e550cfdb0336565bfae7784c0ea1e03bbc19bbe33cffe5a3059e790f549a09f811be3e38f7950c010eec20af37bc7b766d0ad077892ad07af3249f3455689262a49246f5f16f4cb084da339ba5c6c2237deed532a16d3d6c66e0f14e2d2284a0ac48ea1d08c307c86c792f4fd8a3a58b204142874f54185412e264dfc7b7dd6f2b117f8e13a43b2310bdc29b53917b7266e923c0b6398761ccbe604ca642d990ecf476096b98e4bdf97322724afd50f8031d7a26b0d8660d6abcaa4aecf0bf1e67b09daf514f809f01d94c6b6f1acb995969f7ed59ecdffce80a8c69bc6bf7bbd44240455e18e117affee864f5b061352a6dcfd4a65ed60e6a1b739e380fd3bd94e38ef946113f7316607714b8c9fd2caa49772085e31da7e684791f31ec6b23b8311060607b9fd82f9c036c60640ee4c42d141b1ea04586b51290033fe469d7f97e21e6975ebfb02529b10f0594bf3185a8b6dd88a1fe87a2a500a10ac3a9d6af517baab82272a7313bcc333d922544641f5832041b45ca98b1316ce04b0b446582058752d3fffa9b9c26ee43b17ae87fa15d92def0bbf94bd3ae7967d7cf13a585e041fcb5a5893e509713aa091a2f6338f4eb0f6d775ac9518c08df0f8f0f98bbd154db0b77bd0c4e30a69d6c2cb6f4343a9dcbb15fc17209b0f2c50e995fdaa979dcb2901e952de0af89af35251dbd0b410518c75f6cf1405eb7363c78a0a064a3dd1f4e06a933899b677a213e8475dd1d51d2
######################################################################
Server Side Operation
Decrypting station certificate
Loading station public key
Verifying station certificate
Certificate verified
Subject: CN=Shenzhen HuaHong Assembly Co., Ltd.,O=2,L=6,ST=Bus Pirate,C=CN
Issuer: CN=https://buspirate.com,O=Where Labs LLC,C=US
Valid from: 2025-02-08 16:45:45
Valid to: 2025-02-18 16:45:45
Serial Number: 4e1a6290f87eb4b8
Public Key: -----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA57/dKGca6vWCM5nF7+V6
Q5/d6lPah3e72kXg3tJosl6fsohMFx4pyVNVU2N5fdKlnIL19aRJuAF0zjdeVQPq
EPSGchfI9GIUme+u23ETVgmZQKW8YRW74jEvSJApXYPl1krnpUwB+j1K+PO/owmy
RnqDYatPVKKkvvZpde4D6YozTOS5poR6KCsBYK8CbqeBuS8F4egvhXtqoP6IqxCW
222fjoxMXZOfT9MGvcuo2rfOH/M64UBi0Lw0bLaEekBj72uypZpVztuzcVoi+Req
mEdPlnLUCn3WeMNlmHv2TOjOL9G9f9qHh8gYRv+3kgf7hd7WHM7a9sd0ag9ak31w
3QIDAQAB
-----END PUBLIC KEY-----
Certificate created for: 4e1a6290f87eb4b8
Subject: CN=Shenzhen HuaHong Assembly Co., Ltd.,O=2,L=6,ST=Bus Pirate,C=CN
Issuer: CN=https://buspirate.com,O=Where Labs LLC,C=US
Valid from: 2025-02-08 16:45:45
Valid to: 2125-01-15 16:45:45
Serial Number: 4e1a6290f87eb4b8
Public Key: -----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA0x5jt3sPkRpIOrpH4pab
vNi2fPADSP+pzfd+PjjMFR6Srfmh5UP62dUrH4AJ/o/wqxjsmVjYIiZElRCtVJ5I
ZmSKWKikGdfpPm+fKaIC5x9XFpfv7hDg3z7Wxh95nsPWr5FWcgK5ZfgvT92W5/X0
LUDzvs10/Il+PJqLeXqngjFW65eYSpSLcgknAtwb9NniJ5mti+PIrNNNhHbzp9m9
n277Dso/vL7ibnd+XJq/06iqAy9nW3YdVevQ8g0FhgDVeJJXG8hQU1H/ZFF+62Qf
/ZYpug3ZLbGV7Uj4uJpQHof8XLpj6LKJ9ivXtW2aEC6lN4pBJ/Wlw4MWsNpFH+Yd
CwIDAQAB
-----END PUBLIC KEY-----
Encrypted AES Key: 7549f252233ba9c0149fa98fdf08a596b9db3aa74fc8076f5afd2c02ca0ca091f5e4d457bfe939752a840b0617293cd9fea75224c5ffb5d3f9d5aff697c2ff7b5bbb5fb67871d3e4de774f660733c66db5020c770ae1801ef665baf70f574278eca81b881e678a711c40fa1f0e2ab6aff3ccdfb1577caf62d9aa7091832f0fa2b32f546be70d74495c369c538ab16b7b7e96aa9105f0c13355308c9cbbdb5d4c88531c3d1f21b95e3f1c47743342ecf2e48004892d4c10d2c87f34e53205744994747df422bde573f417b8d274a8c1465a0291b1a8a11e2931adc12c4f9202438abdebc5deafb18463a90ac04d4ba7c5d1171e0253c6e1036f5f972c872743b2
IV: 9f9fba8b802f6214edbf975df9da0066
Encrypted Request: 99d55a773c280ec9ee36815043165e7f1a2733ded9dc96982dca0165132bc2b24b464005c5c8cb5e1f98e21626c4db79aafc953c97cb7ebe4f68bf0a2c1ba5c3ba301237172194d02d7fc2a81f93be9d0b4181dda08ca51e003455adf23fb880e0b39e52615224f2f7328fbc93f4221660159cdd4198e4a446afa251727b1b593e5ed5da65b5e6bd3fc4209e7a0e107bcfe54a1b4a83ee01d66f04322c714c0853f36946fb918fda2b89846b6f80f7b56a0fb394243cb6286f021e0f49e84bec11149b287119537fe6dc8b25624f31d82b30e06bfe86a3e7f8e004e24b0be9d09ac515c70087859b4b550a815f504d24a3974cd5418a518a3e30c775ab40f82f27a115efe7ac054de08c117f63e839efa8d29035b7d0642fb5bdf795bd92bc1d9cbd62ba7099ba4f22ae1f0ce62de956597450e5007b8981486a36392a551ebec285b7ea912eed6e65699a0845358ae43152fb26c7c6264b131f81639aba9e4c549c8bfccb3c7cb222c6df71dfa6eb80bc52065fccfeb50613183cbf1d662eea6afc384d1b2848b7c8c24b9d724d48ea260e6885613eee93041842b1aca31d98215fc1e188e14f06704a1f56f262c9e32ac318f362a771e37f834a89f91252f333060a93b6548a168c8b7e124f9184839145cb371cb3ed5c61260132819cb55cda3e7511d79d637da4dfed3b336185f480933ac573f3a81229b41b280ab4745b45b96a7c966dc14f7b1ec0f528230f406ffd589a88a0fc08eaf6344a1a1ba989a89d8745e09b92569ab1d77330daf20a3e8df066f33f15922b60f98a04e16d5f2a3b14f43028ccb8b7e5ab78d42512934ea471255e4c4163262ccdc1364977df098f87b79ba25f63b9d64d4fb9b6bd023ae80c5a65215931f6ea4058cee35c8cd15cff6ddd6626d8d11d1271093cda06844b8eb8f7fd5d64b6f795a3ccaac6cf9536b7e19b189eb485b33888b20e583e5b43f94254e793b084fd11fd82f8e0358d76743698a1d52f5bd13648879eb0f342e10a79bb41a1baa8cad5b06787034bdb8237d4cf4c85f9fcbbb43b95c3f4a90917e72b7d3c2e1d3d09c7c19650685bba0fd17f33dfaa1333378928ee9b723f813f13184acc3900caf97690430f7608e41aeafc0760a1219cc94a3aeccc236600ed012d3775793540cc154b4d9c541f9e644f30a038b0fa127f0b2d75227b995817faa352c57e99dc6eef7a5578a4b9d65fb512eb8918bcdf321e7fafd1231ac5ce71a4929cff44b54ab13a5ab5f7ec868f4d133d3837493165473bc9233dc8bf5ae42f0885934591449c55cbae686ad2220cdba49f42942703b4990d13cdeefc2c162f20c4bdd658dd0be9c9648108d2ff69de9b184e4dc729328034b9a4640149bbb529c670d6f4d3892df8a10884ea0b83db1ee81db76731087a4526e57fb712715bb00b245737f71bb630552cb595ab39e32a9ab59481bfd52a87dc59640cb9758e3d9298a5058bff18e47a2530445b3f05a6a6f6a2e819bbaf7cd148241efc5df495311cf955a8e6396ee44564e0b3db5b74ba6176a60ec29930eb86b7e7e4c7deeb3912d4cef693a273f14ba3b315ccaa308567f8637aa04493af044b256d7e6bca7714e9393270ee875446c63faa78767f427fd71f2627fac6672d305f907528f4e8a51d8e54bcbf77f61b3c
######################################################################
Station Side Operation
Decrypting server certificate
Loading server public key
Verifying server certificate
Certificate verified
Subject: CN=Shenzhen HuaHong Assembly Co., Ltd.,O=2,L=6,ST=Bus Pirate,C=CN
Issuer: CN=https://buspirate.com,O=Where Labs LLC,C=US
Valid from: 2025-02-08 16:45:45
Valid to: 2125-01-15 16:45:45
Serial Number: 4e1a6290f87eb4b8
Public Key: -----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA0x5jt3sPkRpIOrpH4pab
vNi2fPADSP+pzfd+PjjMFR6Srfmh5UP62dUrH4AJ/o/wqxjsmVjYIiZElRCtVJ5I
ZmSKWKikGdfpPm+fKaIC5x9XFpfv7hDg3z7Wxh95nsPWr5FWcgK5ZfgvT92W5/X0
LUDzvs10/Il+PJqLeXqngjFW65eYSpSLcgknAtwb9NniJ5mti+PIrNNNhHbzp9m9
n277Dso/vL7ibnd+XJq/06iqAy9nW3YdVevQ8g0FhgDVeJJXG8hQU1H/ZFF+62Qf
/ZYpug3ZLbGV7Uj4uJpQHof8XLpj6LKJ9ivXtW2aEC6lN4pBJ/Wlw4MWsNpFH+Yd
CwIDAQAB
-----END PUBLIC KEY-----
Burn to Bus Pirate OTP:
unsigned char cert_der = { 0x30, 0x82, 0x03, 0x30, 0x30, 0x82, 0x02, 0x18, 0xa0, 0x03, 0x02, 0x01, 0x02, 0x02, 0x08, 0x4e, 0x1a, 0x62, 0x90, 0xf8, 0x7e, 0xb4, 0xb8, 0x30, 0x0d, 0x06, 0x09, 0x2a, 0x86, 0x48, 0x86, 0xf7, 0x0d, 0x01, 0x01, 0x0b, 0x05, 0x00, 0x30, 0x46, 0x31, 0x0b, 0x30, 0x09, 0x06, 0x03, 0x55, 0x04, 0x06, 0x13, 0x02, 0x55, 0x53, 0x31, 0x17, 0x30, 0x15, 0x06, 0x03, 0x55, 0x04, 0x0a, 0x0c, 0x0e, 0x57, 0x68, 0x65, 0x72, 0x65, 0x20, 0x4c, 0x61, 0x62, 0x73, 0x20, 0x4c, 0x4c, 0x43, 0x31, 0x1e, 0x30, 0x1c, 0x06, 0x03, 0x55, 0x04, 0x03, 0x0c, 0x15, 0x68, 0x74, 0x74, 0x70, 0x73, 0x3a, 0x2f, 0x2f, 0x62, 0x75, 0x73, 0x70, 0x69, 0x72, 0x61, 0x74, 0x65, 0x2e, 0x63, 0x6f, 0x6d, 0x30, 0x20, 0x17, 0x0d, 0x32, 0x35, 0x30, 0x32, 0x30, 0x38, 0x31, 0x36, 0x34, 0x35, 0x34, 0x35, 0x5a, 0x18, 0x0f, 0x32, 0x31, 0x32, 0x35, 0x30, 0x31, 0x31, 0x35, 0x31, 0x36, 0x34, 0x35, 0x34, 0x35, 0x5a, 0x30, 0x68, 0x31, 0x0b, 0x30, 0x09, 0x06, 0x03, 0x55, 0x04, 0x06, 0x13, 0x02, 0x43, 0x4e, 0x31, 0x13, 0x30, 0x11, 0x06, 0x03, 0x55, 0x04, 0x08, 0x0c, 0x0a, 0x42, 0x75, 0x73, 0x20, 0x50, 0x69, 0x72, 0x61, 0x74, 0x65, 0x31, 0x0a, 0x30, 0x08, 0x06, 0x03, 0x55, 0x04, 0x07, 0x0c, 0x01, 0x36, 0x31, 0x0a, 0x30, 0x08, 0x06, 0x03, 0x55, 0x04, 0x0a, 0x0c, 0x01, 0x32, 0x31, 0x2c, 0x30, 0x2a, 0x06, 0x03, 0x55, 0x04, 0x03, 0x0c, 0x23, 0x53, 0x68, 0x65, 0x6e, 0x7a, 0x68, 0x65, 0x6e, 0x20, 0x48, 0x75, 0x61, 0x48, 0x6f, 0x6e, 0x67, 0x20, 0x41, 0x73, 0x73, 0x65, 0x6d, 0x62, 0x6c, 0x79, 0x20, 0x43, 0x6f, 0x2e, 0x2c, 0x20, 0x4c, 0x74, 0x64, 0x2e, 0x30, 0x82, 0x01, 0x22, 0x30, 0x0d, 0x06, 0x09, 0x2a, 0x86, 0x48, 0x86, 0xf7, 0x0d, 0x01, 0x01, 0x01, 0x05, 0x00, 0x03, 0x82, 0x01, 0x0f, 0x00, 0x30, 0x82, 0x01, 0x0a, 0x02, 0x82, 0x01, 0x01, 0x00, 0xd3, 0x1e, 0x63, 0xb7, 0x7b, 0x0f, 0x91, 0x1a, 0x48, 0x3a, 0xba, 0x47, 0xe2, 0x96, 0x9b, 0xbc, 0xd8, 0xb6, 0x7c, 0xf0, 0x03, 0x48, 0xff, 0xa9, 0xcd, 0xf7, 0x7e, 0x3e, 0x38, 0xcc, 0x15, 0x1e, 0x92, 0xad, 0xf9, 0xa1, 0xe5, 0x43, 0xfa, 0xd9, 0xd5, 0x2b, 0x1f, 0x80, 0x09, 0xfe, 0x8f, 0xf0, 0xab, 0x18, 0xec, 0x99, 0x58, 0xd8, 0x22, 0x26, 0x44, 0x95, 0x10, 0xad, 0x54, 0x9e, 0x48, 0x66, 0x64, 0x8a, 0x58, 0xa8, 0xa4, 0x19, 0xd7, 0xe9, 0x3e, 0x6f, 0x9f, 0x29, 0xa2, 0x02, 0xe7, 0x1f, 0x57, 0x16, 0x97, 0xef, 0xee, 0x10, 0xe0, 0xdf, 0x3e, 0xd6, 0xc6, 0x1f, 0x79, 0x9e, 0xc3, 0xd6, 0xaf, 0x91, 0x56, 0x72, 0x02, 0xb9, 0x65, 0xf8, 0x2f, 0x4f, 0xdd, 0x96, 0xe7, 0xf5, 0xf4, 0x2d, 0x40, 0xf3, 0xbe, 0xcd, 0x74, 0xfc, 0x89, 0x7e, 0x3c, 0x9a, 0x8b, 0x79, 0x7a, 0xa7, 0x82, 0x31, 0x56, 0xeb, 0x97, 0x98, 0x4a, 0x94, 0x8b, 0x72, 0x09, 0x27, 0x02, 0xdc, 0x1b, 0xf4, 0xd9, 0xe2, 0x27, 0x99, 0xad, 0x8b, 0xe3, 0xc8, 0xac, 0xd3, 0x4d, 0x84, 0x76, 0xf3, 0xa7, 0xd9, 0xbd, 0x9f, 0x6e, 0xfb, 0x0e, 0xca, 0x3f, 0xbc, 0xbe, 0xe2, 0x6e, 0x77, 0x7e, 0x5c, 0x9a, 0xbf, 0xd3, 0xa8, 0xaa, 0x03, 0x2f, 0x67, 0x5b, 0x76, 0x1d, 0x55, 0xeb, 0xd0, 0xf2, 0x0d, 0x05, 0x86, 0x00, 0xd5, 0x78, 0x92, 0x57, 0x1b, 0xc8, 0x50, 0x53, 0x51, 0xff, 0x64, 0x51, 0x7e, 0xeb, 0x64, 0x1f, 0xfd, 0x96, 0x29, 0xba, 0x0d, 0xd9, 0x2d, 0xb1, 0x95, 0xed, 0x48, 0xf8, 0xb8, 0x9a, 0x50, 0x1e, 0x87, 0xfc, 0x5c, 0xba, 0x63, 0xe8, 0xb2, 0x89, 0xf6, 0x2b, 0xd7, 0xb5, 0x6d, 0x9a, 0x10, 0x2e, 0xa5, 0x37, 0x8a, 0x41, 0x27, 0xf5, 0xa5, 0xc3, 0x83, 0x16, 0xb0, 0xda, 0x45, 0x1f, 0xe6, 0x1d, 0x0b, 0x02, 0x03, 0x01, 0x00, 0x01, 0x30, 0x0d, 0x06, 0x09, 0x2a, 0x86, 0x48, 0x86, 0xf7, 0x0d, 0x01, 0x01, 0x0b, 0x05, 0x00, 0x03, 0x82, 0x01, 0x01, 0x00, 0x04, 0xdb, 0x3b, 0x4c, 0xf6, 0x19, 0xfe, 0xdd, 0xa9, 0x89, 0x88, 0xb7, 0xeb, 0x74, 0x22, 0x76, 0xc6, 0x12, 0xfa, 0xd1, 0xe3, 0x83, 0x7b, 0xd9, 0x84, 0x9c, 0x7d, 0x1d, 0xec, 0x74, 0x50, 0xcf, 0x2e, 0xd5, 0x98, 0xf2, 0x35, 0x1e, 0xf3, 0xbb, 0x98, 0x7d, 0x90, 0xb1, 0x3d, 0xa5, 0x4c, 0x48, 0x27, 0x1b, 0x40, 0x7f, 0xcd, 0x4c, 0x75, 0x8e, 0x1c, 0x94, 0xa3, 0xb0, 0x9b, 0x4f, 0x39, 0x8a, 0x90, 0xbe, 0xc9, 0x86, 0xe4, 0xf1, 0xd8, 0x28, 0x64, 0x8e, 0x05, 0x75, 0x5b, 0xe0, 0xe5, 0x2a, 0xee, 0x27, 0x4b, 0x58, 0x25, 0xd4, 0x58, 0x74, 0x45, 0xa1, 0xb9, 0x8f, 0xaa, 0x90, 0x2a, 0x12, 0x1e, 0x90, 0xb9, 0x74, 0x70, 0x69, 0x7f, 0x1f, 0x50, 0x43, 0x23, 0xba, 0x4d, 0xa1, 0xb9, 0xae, 0x8e, 0xb1, 0xf2, 0x2f, 0x7f, 0x19, 0x37, 0xce, 0xab, 0x07, 0x84, 0x4b, 0xa4, 0x42, 0xbd, 0x34, 0x28, 0x0d, 0x03, 0x50, 0x31, 0x1d, 0xfe, 0xfe, 0x08, 0xd0, 0x6b, 0xf0, 0x69, 0x6d, 0x3b, 0xad, 0x10, 0xfd, 0xed, 0x29, 0xd0, 0x22, 0x2f, 0xe0, 0xed, 0xfc, 0x22, 0xe7, 0x4c, 0x8b, 0xf2, 0xeb, 0x52, 0xcf, 0xb4, 0x39, 0x8a, 0xc9, 0xb8, 0x2d, 0x95, 0x3d, 0x0d, 0x70, 0x43, 0xea, 0x6f, 0xb3, 0xc1, 0x6b, 0xb7, 0xc1, 0xd6, 0x03, 0xdc, 0xe7, 0x50, 0xf9, 0x52, 0x4c, 0x54, 0x5d, 0x1d, 0x36, 0x35, 0x35, 0x61, 0xde, 0x85, 0x34, 0xb0, 0xc2, 0x53, 0xdf, 0x3a, 0x0e, 0x12, 0x60, 0xe9, 0xec, 0x7b, 0x61, 0x15, 0xdb, 0x52, 0x6f, 0x34, 0x3c, 0x3f, 0x4c, 0x5e, 0xbd, 0xb9, 0x0d, 0x38, 0xe5, 0x26, 0x3f, 0x7b, 0x72, 0x1d, 0x9f, 0xc7, 0x60, 0x02, 0x2f, 0x7f, 0x85, 0x52, 0x07, 0x1d, 0x2f, 0x01, 0x3e, 0xdd, 0xb5, 0xb5, 0x97, 0x1a, 0xc4, 0xd5, 0xaf, 0x50, 0x7c, 0xb4, 0xa4, 0x43, 0xf1 };
unsigned int cert_der_len = 820;
######################################################################
- Station generates a private key and we save the pubic key on the server manually
- Server has a private key and we save the public key on the station manually
- Station reads RPi ID and creates a signed request cert with Rpi serial number. AES encrypt the contents and encrypt the AES key with the server public key
- Server decrypts the request cert and verified against the known-good station public key
- Server creates the Bus Pirate cert, encrypts with AES and the station public key
- Station decrypts and verifies the Bus Pirate cert with the know-good server public key
- Station converts to DER and burns to OTP
The first row (2 bytes) of the cert space should contain the byte (or row) count.
Looks good! Just a few comments:
The key exchange in steps 1 and 2 are important; I assume you have control over both ends, so that helps.
Steps 3, 4, 5, and 6: is the encryption necessary? The CSR is signed and the cert is signed and can be verified at both ends with the public key. That ensures integrity and authenticity. I don’t know if confidentiality is required here?
Probably the biggest area is of vulnerability is the storage of the private key on the manufacturing station. A threat actor with that key can get signed certificates. Some possible mitigations to that:
- Rotate mfg station keys often
- Limit physical access to mfg station (difficult in hostile mfg environments)
- Secure the communications channel between the manufacturing station and the server
- Strong authentication from mfg station to server
- VPN between the mfg station to server
- You know when manufacturing is happening, so limit the server availability to known times
Definitely! Could the key security be improved with a USB hardware dongle, which prevents key material from escaping its boundary, and provides the necessary crypto primitives?
If so, then each manufacturing run, a new cert+CSR from that mfg station could be generated, with validity limited to the active factory hours for the day. Audit the dongles at the start of the day, and if one is missing, don’t enable the server until you know which one(s) to reject requests from.
While it can be less vulnerable, the server’s key has higher risk if lost, and generally should have at least as strong protection.
I noticed today that YubiKey has a tiny HSM.
But, once you see the costs and think through the security overhead, it may be worth considering a cloud-provider’s key vault rather than managing it yourself.
Any reasonable HSM will include M of N key backup / restore capability. Another launch point for learning more about securely backing up critical keys can be read various places. Typically, only your root key(s) need this type of backup. Since you are personally implicitly trusted, you can generate the portions yourself, and give a portion to an attorney, put one in your safe deposit box, another to trusted friends to store, etc.
[[ Typically, these portions are generated on air gapped machine, recorded in a non-electronic form (e.g., hand-written), stored in opaque containers with tamper-evident seals, viewed only in secure locations w/o recording devices, etc. You can of course adjust based on your risk aversion. ![]() ]]
]]
For actual production, I’ve used hardware HSMs, air gapped master private keys, etc. The HSM did the signing without ever exporting private key material.
For what we’re talking about here, @ian maintaining physical control of the private key is probably sufficient. Is the threat of someone gaining physical access to his location to steal the key sufficient to justify something more than that?
To be honest, I don’t trust 3rd party cloud security for keys. I know that many organizations use them, but it’s always been off the table for any use I’ve been involved with; hence the local HSMs.
I’ve seen that Yubikey HSM; I’d love to play with one, but not at that cost ![]()
I had a look at Microsoft authenticator just for giggles. For verifying the station each day. This will all happen in our office while Abin does 4th pass quality control so I just can’t justify it.
It’s a fun thought experiment, but Abin has been with us for years and he’s a stand up guy.
The other aspect is that the station public key will only be authorized on the sever for 1. Duration of 4th pass QC (currently 1 to 2K), and 2. For a fixed number of uses. Even if Abin was pulling a night shift we would know pretty fast and it would be limited.
There could be a case for key rotation every 100 uses? Or whatever our calculated historic daily throughput is?
That gives you a lot of control for each production run.
You could rotate keys each run. Maybe a script that generates the keys and sends you the public half. You know when there’s going to be a run, so when to expect a new public key.
It’s not secure enough for a lot of things, but probably for enough for this.
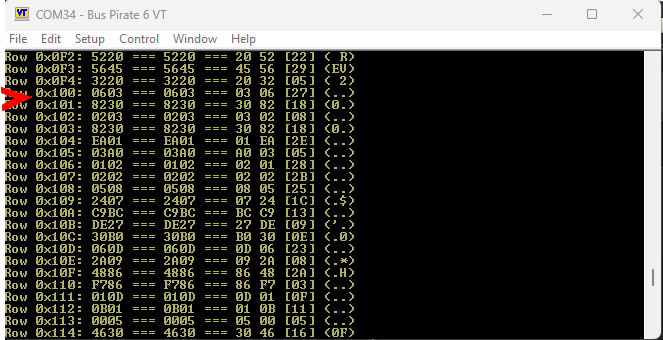
Success installing a cert to OTP starting at row 0x100 (length at 0x100, data starts at 0x101).
Retrieving the cert from OTP and validating it.
Still a lot of polish needed, but most of the components seem to be there.