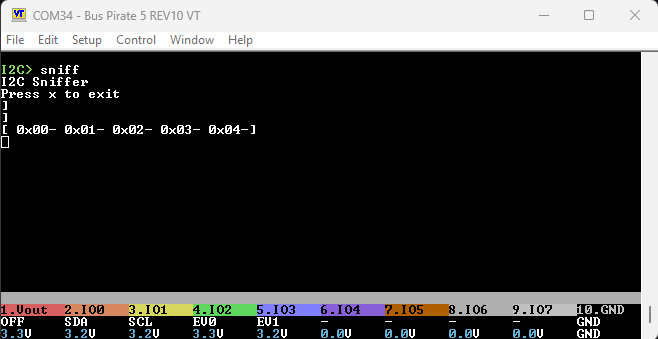
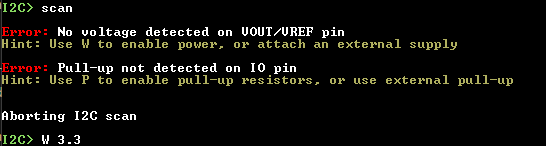
Continuing the discussion from I2C "promiscuous/sniffing" mode?:
Summary thus far...
- Billms posted asking for way to snoop on I2C, specifically on between two HDMI devices.
- Ian noted best bet is Logic Analyzer mode of the BP5 + Pulseview / Sigrok for decoding
- MS3FGX asked if this meant BP3 I2C sniffing features will never arrive
As you know, technically, anything that’s missing from the BP5 (but was in BP3) could be implemented eventually. Generally, backwards compatible features have had someone familiar with how they worked on BP3 who drove the feature, provided test cases, etc. This could be Ian, but more often it’s someone who was relying upon the feature in BP3, and wants to secure an upgrade path.
The way I read Ian’s response, he was helping that user move forward with their problem as rapidly as possible, not saying a feature would never be part of main firmware.
Since I am not familiar with the I2C “snooping” feature in BP3, could you help fill in some details on your question for me?
- What features are you specifically looking for?
- Are you looking for some type of scripting compatibility, or individual commands, or … ?
- Can you help me understand some use cases where it’s better to have a built-in capability in the firmware? (vs. capturing a trace for decoding on PC … e.g., if the BP3 allowed to mostly sniff, but then intentionally corrupt transmission in some way? e.g., other types of fault-injection?)
Thanks!