Background
I’m a member of the IoT Hacker Hangout discord group, and as part of looking into the security of an Internet-connected webcam, I removed a WSON8 SPI NAND from the unit, and wanted to dump its contents.
First Learnings
The BusPirate’s WSON8 plank made connecting it up really easy. ![]() I then tried to use the firmware’s built-in CLI to read a few bytes, but the built-in support wasn’t working.
I then tried to use the firmware’s built-in CLI to read a few bytes, but the built-in support wasn’t working.
Turns out I have been “lucky” with all my prior SPI NAND … the W25N01GB was the first chip I messed with that didn’t have the same sequence for chip identification:
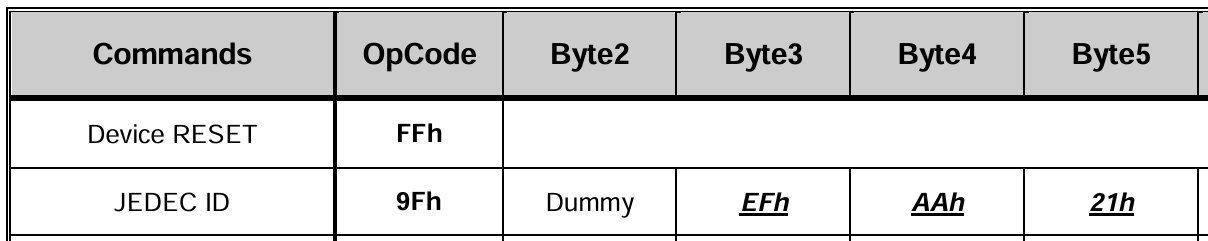
[0xFF] d:1000 [0x9F r:3]
Aka: Send the reset command, wait a second, then send the JEDEC ID command and read the three-byte response.
On this chip, however, the JEDEC ID isn’t reported immediately … it’s offset by a one-byte delay, shown as “Dummy” on the datasheet:
Digging deeper, I learned lots of unhappy things about the JEDED ID. It’s only “practical” use is to distinguish between a limited set of predetermined devices … not as a general identification technique. For example, there are subgroups for manufacturer ID … and the IDs themselves are not actually unique in the field.
So, I learned the “basic” identification flow is nowhere near sufficient for a general identification. I have some thoughts on improving this (including subgroups), but … I just needed to get the contents…
Second Learnings
Unfortunately, it turned out that a number of other key commands also needed delays, including reads. Thus, this wouldn’t be a simple change if I updated the core BusPirate firmware’s SPI NAND commands.
BPIO2 to the rescue!
But that’s OK! The BusPirate’s BPIO2 support allows prototyping in many languages!
Using the BPIO2 binary interface, I was able to quickly whip up some Python script which dumped the contents.
Interestingly, there was at least one other person on that project who also wanted to use the BusPirate for this, so I was able to shared my (hacked) Python script on that forum.
BusPirate is truly the swiss-army knife …
While I probably could have used some other program, the convenience of dropping the WSON8 chip into a well-made plank, and the simplicity of using the BPIO2 interface from host-side scripts, really showed off the power of the BusPirate!